Back Story
One of the many reasons I love working for the BioTeam is that we are pretty much a 100% virtual and entirely distributed company – our biggest fixed physical asset at this point are the racks of colocation space that we rent within an a Boston-area datacenter (and even that is shrinking as we rely more heavily on Citrix XenServer virtualization and the Amazon cloud).
 |
| This is my “office” |
All BioTeam employees work from home (or coffeeshops, airport lounges or hotels) when not traveling on business or working onsite with clients.
This means that all of the “stuff” required to support a real company must also be largely virtual and distributed. Over the years as our little group has grown we’ve gotten the chance to kick the tires and use “for real” a number of different products and technologies that help us stay agile, distributed and nimble.
The other thing I like about this company is how we all share the burden of doing all the daily behind the scenes stuff required to keep the company alive and making payroll. The internal load-balancing that we do helps keep our staff ratio amazingly productive – we have no middle management and almost no “overhead” positions. Of the 10 current employees at the time of this post, 9 of us are client-facing and directly billable consultants and/or software developers.
My “internal” responsibilities fall into two categories – I’m the goto guy for HR stuff like benefits, insurance and administering the company 401K retirement plan. I’m also the internal Infrastructure Guy’ responsible for company macbooks, iphones, verizon mifi’s and all of the public, private and cloud infrastructure we use to run our business and development environments.
I’ve spent 10+ years in the trenches building this small virtual company and figured it might be useful to blog about some of the behind the scenes things that make our business and professional lives easier. Consider this post the first in a series of articles on products, vendors, services and technology that we use to enable ourselves.
 |
| VPN in action at a local Starbucks |
VPNs for Small Business
I’ll admit that we were slow to jump on the VPN bandwagon, primarily the following reasons:
- Our colo provider gave us a class-C netblock with 254 usable IP addresses, making it easy to just stick boxes and services on the public internet
- Our employees are SSH gurus and have mad skillz with SSH tunnels and crazy forward and reverse port forwarding and encrypted tunnel setups
We’ve always had VPN-capable hardware as we are fans of Juniper devices for hardware firewalls, content screening and deep packet inspection. The various Netscreen and SSG devices we have are all VPN-capable.
With the exception of a few testbed site-to-site VPN links and the more recent Amazon VPN deployment demo we’ve never used the Juniper devices for “serious” client/staff VPN use. Why not? … mainly because they are a usability nightmare for anyone who is not an IPSEC networking genius. The “easiest” way to get them to work cleanly and easily with Mac OS X would requires expensive client licenses for VPNTracker software from Equinox.
 |
| Fantastic visual metaphor – When you see a “light” coming from the “tunnel”, the VPN link is active. |
Why everyone needs VPNs
For us, easy client-based VPN functions are no longer a “nice to have” thing, they are an absolute “must have” requirement for operating a modern company with a mobile workforce.
Why? Here are just a few reasons
- Hostile Wi-fi networks. Our employees are extremely mobile (heck I’m writing this post from a Starbucks right now) and often end up connecting to public hotel, airport and coffeeshop wireless access points. These are not safe places to use a laptop for any reason, personal or work. Just do a google search for “firesheep” to see how easy it is for a nonskilled person to swipe credentials or hijack browser sessions on shared public networks and subnets. It is an absolute requirement that our employees have a transparent and easy to use method to encrypt everything they are doing while using public networks
- Critical IP address shortage. Our glorious past of having a Class-C netblock of our own with 254 usable IPs are soon to be history. Public facing IP addresses are in short supply and we need to respond to this by moving 95% of our servers and services onto private internal networks. Facing a vast reduction in the number of public IP addresses we control will require us to provide VPN service to our team.
- Unaccountable Government Intrusion. As a tech-heavy company we are gravely concerned with recent actions of the US Government making arbitrary and zero-accountability searches of electronic devices at borders and points of entries. Devices are searched and copies of data may be made with zero ability to find out what is being done with that data, who will access it and how long it will be stored or archived. Our staff often have access to confidential data and material that we have signed NDA agreements around. For legal and moral reasons it is our duty to keep this information safe and secure. Our past practice of using whole disk encryption (WDE) may no longer be sufficient if our staff are forced to divulge passwords or encryption keys. In 2011 BioTeam is planning for a future where international travel requires the use of a “naked laptop” stripped down to nothing more than VPN and Remote Desktop software installations. The only protection against warantless search and seizure is to transit borders with nothing that can be seized. VPNs and remote desktop software make this possible.
VPN Options
- DIY – We could have built our own solution using free and open source software. Not an option considering how difficult IPSEC implementation and troubleshooting can be in the real world.
- Use our existing Juniper devices. We don’t use Windows so we can’t use the Juniper client software stack. Our firewall/IDS products don’t have SSL-VPN features that other, more specialized Juniper devices provide. Setting up site-to-site VPNs was such a hassle that we didn’t even want to consider using the Juniper systems for client VPN access, especially after figuring in that we’d likely need commercial VPN software for our OS X macbook laptops.
- Dedicated SSL VPN hardware. Probably a good choice but our need for multiple devices likely pushes the acquisition and deployment costs well into the “several thousand dollars” range. Something we’d like to avoid if possible until we really need the speed and features the dedicated access devices provide.
- Hosted VPN. We’d rather not pay a monthly per-user fee for this service if we can avoid it.
Our Choice
We are currently using a combination of commercial and free software that requires a very reasonable infrastructure and cost for each VPN endpoint we roll out:
- One tiny CentOS linux VM
- One public facing IP address
- $50/year for every 10 concurrent client connections we need
We are doing this via two products:
OpenVPN Access Server
 |
 |
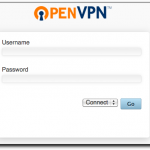
| Users login to a web page to download their VPN configuration profile. |
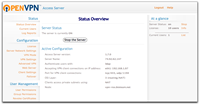
What the administrator sees |
I love this product, It took all of two minutes to download and install a single Access Server .RPM file onto our CentOS linux VM.
Installing our wildcard *.bioteam.net SSL certificate took another minute and configuring the Access Server to authenticate clients against our external LDAP server took perhaps 10-15 minutes of experimentation and testing before we got all the settings correct.
Less than 5 minutes after configuring the OpenVPN access server to point at our LDAP server for username and password authentication I was able to login to the system and download a user-specific VPN client configuration file that is drop-in compatible with the fantastic and free Tunnelblick OS X client software.
The cost? Right now you can get OpenVPN Access Server up and running for free if you only need 2 concurrent client connections. Adding additional concurrent connections is $5/user with a minimum purchase of 10 users at a time. Our total cost was thus just $50.00 USD for a VPN server solution that trivially installed onto our existing virtualization environment.
Tunnelblick
 |
| Tunnelblick |
Tunnelblick is the client-side solution we install on our staff laptops. This is no longer strictly necessary with OpenVPN Access Server as that system is capable of providing SSL-VPN along with downloadable client binaries for common operating systems.
However, we like what Tunnelblick does and how trivial it is to integrate with OpenVPN Access Server. It’s a fantastic and free solution for Apple OS X users.
Operational Burden
People who know our work in the IT/HPC space for biotech and other life science clients know how we focus on the operational and administrative burden of things. We look at our VPN service via the same cynical eye — how easy is it to manage and how easy is it for our employees to use?
The answer is that the solution is damn easy both to manage as an administrator and use as an employee.
All a BioTeam employee needs to do is this:
- Download and install Tunnelblick
- Login to our VPN Access Server site
- Download the user-specific VPN configuration profile
- Save the profile to a Tunnelblick folder
- Restart Tunnelblick
After that the VPN service is integrated with Tunnelblick via an easy to see/use icon in the top desktop menu bar. Enabling, disabling and checking status is a simple one-step operation.
It “just works” and that is what we like to see. Making the service non-intrusive and easy to use is key in ensuring that staff actually make use of it.
If you made it this far, thanks for reading. We’d love to see your comments and feedback. What do you use for secure remote access in a hostile network environment?


