Using PIV smart cards for HHS VPN login with Mac OS X 10.10 Yosemite
Note: This entire post is basically google search bait designed to (hopefully) allow others struggling with the same issues to save a bit of time. Hope it helps!


October 30, 2014 Update
There is an active Citrix support thread on the “no valid certificates found” issue. If this is bothering or interesting you, you may want to monitor this URL: http://discussions.citrix.com/topic/357156-no-certificate-found-at-windows-logon-screen-for-smartcard-authentication/
October 24, 2014 Update
The bulk of this post concerns the $29 Pkard product from Thursby which is the first I found with explicit OS X 10.10 support. I just had a chance to test the new Yosemite 10.10 compatible free SmartCard utility from Centrfy mentioned here: http://www.centrify.com/mac/smartcard/free-smart-card-for-federal-military-cac-piv.asp
. Long story short: It works to get past the VPN gateway but throws the same “no valid certificates found” error when trying to login to the Windows desktop via a Citrix Receiver client. Still no idea why this is happening – on other versions of OS X my smart card credentials transparently passed onto the OS. Still – consider the Centrify software if you don’t want to spend $29.
Short Summary
I need to use a HHS PIV card to remotely access computer systems from a brand new Macbook air running OS X 10.10 Yosemite. As of the time I wrote this article, the state of freely available open source software for PIV smart card support on Yosemite is pretty lacking. This will change but if you are in a hurry (as I was) the best thing you can do in the short term is pay $29.95 for the Thursby PKard software from http://www.thursby.com/products/pkard-mac — it installed seamlessly and allowed me to login via VPN although for some reason my certificates were not passed on to the Windows remote desktop system, hopefully I don’t need the $179 “ADmitMac” product for that.
I expect the state of open source smart card and tokend implementations to get better and more easily usable on Yosemite so I may only be using the Thursday product for a short time. It did, however work fast and got me successfully logged onto the remote VPN server.
Current status: Thursby PKard software works well on Yosemite for VPN access but the Windows desktop I get sent to via a Citrix client reports “no valid certificates” and I’m forced to use my standard user login name and password to complete the final authentication. This was not something I needed to do on OS X 10.7 or 10.7 with the open source smart card software stack.
Background
I do some subcontracting work for a few US Government agencies, one of which requires me to be able to connect remotely to US.GOV networks and infrastructure. The way I connect is via a federal standard PIV Card which is a very cool physical badge that doubles as a holder of biometric and personal crypto certificate information. When I’m trying to physically enter a building the PIV card is my secure photo ID badge (with backup biometrics and fingerprints stored o it) — when I try to enter a US Government network “virtually” the same PIV card doubles as VPN access device because it contains a personal set of crypto keys that uniquely identify me. Two-factor authentication is achieved by having to punch in a PIN code when my certs are presented to the remote system. It’s a very slick and interesting system.
From what I can tell, PIV cards are very similar to the CAC cards carried by military members that are often required for secure web browsing and access to military resources In fact, when searching the internet for PIV assistance you will find that some of the best help resources are coming from the military CAC-user community. A perfect example of this is https://militarycac.com/macnotes.htm and https://militarycac.com/cacenablers.htm – the site that I turned to first when looking for OS X Yosemite PIV/smartcard status info.
My Gear
- SCM SCR3500 Smart Card Reader – Amazon Link: http://amzn.com/B00434WQVU
- Belkin flexible USB adapter – Amazon Link: http://amzn.com/B000BK107G
- Macbook Air running OS X 10.10 Yosemite
Getting the PIV card to work on 10.10 Yosemite
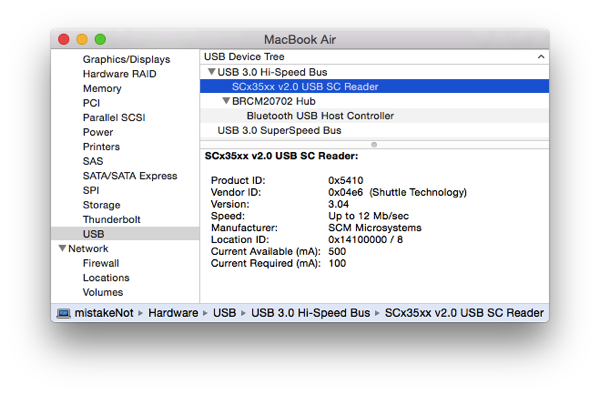
Verify your reader works
Attach your reader, use the OS X “About this Mac” -> “System Report” function to verify that your computer and OS actually see and recognize a smart card device:
Buy and install the PKard software


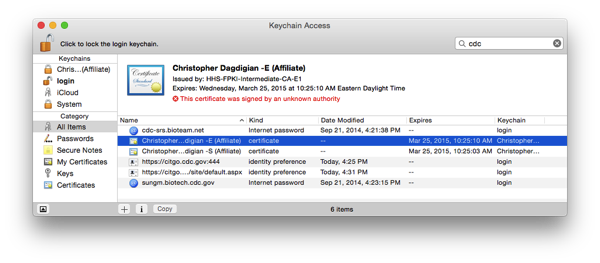
Launch OS X Keychain Assistant
What you want to see is the certificates and credentials that are stored on the smart card. If your USB reader and the PKard software are working, Yosemite 10.10 can now “see” the crypto info stored on the PIV card
Fix the Trust Chain (If your PIV certificate is not trusted)
This may not be an issue for an upgraded system but on my brand new laptop my host OS was missing the intermediate certificate trust chain. Keychain Assistant helpfully throws up the red text saying: “This certificate was signed by an unknown authority”
OS X Yosemite does not “trust” the Certificate Authorities that signed my PIV card certificates.
The solution is to go out and install the intermediate certificates necessary to build the full lenght trust chain.
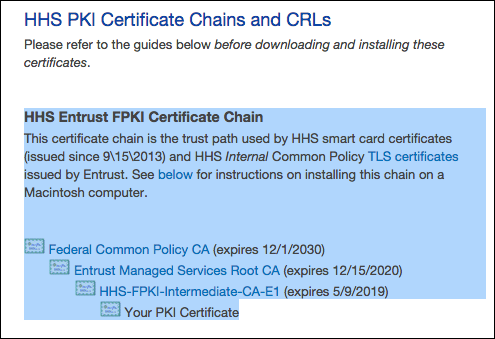
The source of trust chain certificates almost certainly depends on what agency you work for or are trying to access. In my case I needed the US GOV Health and Human Services (HHS) intermediate certificates and the best online resource I found for HHS certificates needed for PIV cards is actually over on a NIH hosted site:
https://ocio.nih.gov/Smartcard/Pages/PKI_chain.aspx
I downloaded and installed the “HHS Entrust FPKI Certificate Chain” from the above website:
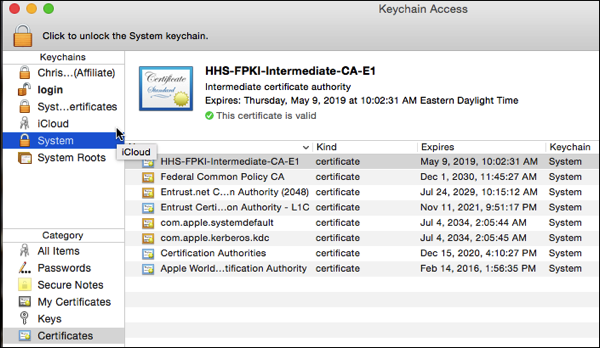
Installing the certificates results in a chain of trust that culminates with your personal PIV certificates being recognizes as trusted:
Now Test
At this point you have a recognized USB card reader, your personal PIV certificates are visible to Mac OS X and the trust chain is complete. This should be all you need to access or login to PIV-enabled websites.
I removed screenshots showing the portal site I was logging into out of paranoia so I can’t show examples of successful logins. I’ll just show this OS X window which is the system prompt you get when your certificate is being used and the host OS wants to verify your PIN code as part of the two-factor authentication process.
If you see this, this is your PIN entry prompt and it means that stuff is generally working:
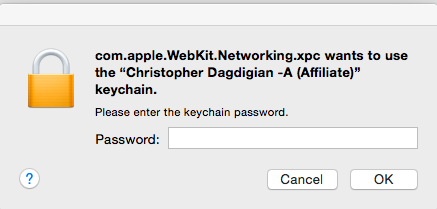
Remember that this is where your PIN goes, ignore the system text about “keychain password” …
Minor Issue
Using the steps outlined above I can successfully authenticate to the remote access environment I need to use on a daily basis. However, on my older laptop my PIV card credentials were transparently passed onto the Windows OS as well and I was not prompted for a second login.
That is not the case now. After getting past the VPN, the remote desktop session can’t see my PIV certificate and I have to fallback to using standard AD username and password. Not optimal but it works for my purposes.
Longer term I want this issue to go away. I’m not sure if it’s a Citrix Receiver issue or perhaps this is a designed-in behavior of the Thursday software designed to upsell software that offers more functionality. I was willing to pay $29.99 for the functionality I needed and the software and documentation is great but I’m not going to shell out $179 for SSO access to a Windows Desktop.

I’m going to keep researching this and will keep an eye on the state of open source / free smart card services for Yosemite 10.10. Will update this post as needed.


